
A Successful Business is a Growing Business
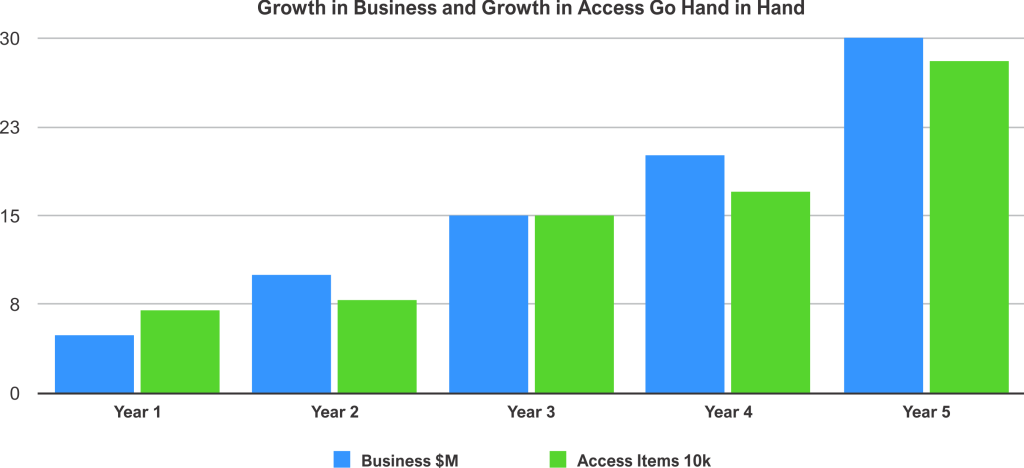
You and your colleagues have worked hard to get to where you are today. You’ve never been larger and your business is still growing. New people, new ideas and new systems to handle the workload never stop coming in.
This growth in capabilities comes at a cost though and managing the Identity and Access required to scale up can seem like an overwhelming task. The good news is that you know that a well developed Role Based Access Control (RBAC) program can drastically reduce the effort required to ensure the proper access for your users without becoming a nightmare of manual access request and attestation efforts.
What makes a successful Role Based Access Control Program?
A Successful Role Program is defined as one that:
-
Produces as few roles as possible
-
That cover as much access as possible
-
For as many people as possible
-
With roles that align to existing control structures
-
As swiftly as possible
-
And ends when there are no more valuable roles
This is a lot of objectives to balance and it requires experience and capabilities to make sure that its done right. Our team at CyberSolve has a combination of decades of experience in RBAC and cutting-edge capabilities in the form of our Role Mining Analysis Tool-suite to make sure that the optimum set of roles is created as swiftly as possible.
Role Model Analysis is the Key Differentiator Between a Role Program that succeeds and a Role Program that Wastes Your Time
Role Model Analysis means weighing the value of different potential role models before deciding which one to pursue.
All Role Programs develop a Role Model, which is the set of roles and the order in which you decide to build them. Not all Role Programs deliberately choose the role model that best suits your IAM Environment and this prevent you organization from benefitting from your RBAC Effort. Before embarking on a large scale role creation process you’ll first want to determine if the way in which you intend to create roles is right for your business.
Finding mathematical certainty behind answering which roles to create used to require hundreds of man hours of manually collating spreadsheets. This could easily result in an organization changing faster than it can be analyzed, resulting in wasted effort.
How do we conduct a Role Model Analysis in a timely fashion?
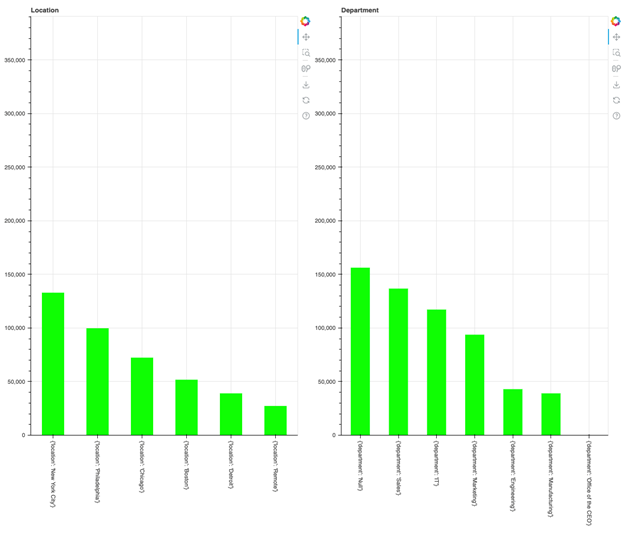 A graph of the relative value of two different ways to create roles. In this particular data set the greater value of the “Department” role candidates suggests that it’s a superior way to build roles than based on Location.
A graph of the relative value of two different ways to create roles. In this particular data set the greater value of the “Department” role candidates suggests that it’s a superior way to build roles than based on Location.
The good news is that the old ways of figuring out which roles to build, the order to build them, and what to put in them are in the past. You don’t need a team of business analysts working for months sifting through access in Excel because we’ve written software to automate this process and put the results in front of key decision makers in a fraction of the time it used to take. By leveraging Data Science tools and the power of modern processors we’re taking the leg-work out of Role Based Access Control programs, this means less time is spent on collating data freeing up more time for making the decisions that really matter.
What does an RBAC Program with Role Model Analysis Program look like?
There are three steps we take to complete and RBAC program at a client and Role Model Analysis is only the first. We’re building you roles throughout all three steps, at an increasing pace as we develop your IAM teams ability to develop roles faster.
Deliverables By Phase

1. Find Your Role Model
-
Role Model Analyses
-
Entitlement Analyses
-
RBAC Program Requirements
-
A Pilot Set of Roles (>20)
By the end of this phase you will know what roles you should build and the order in which they should be built along with how to configure your IAM System to benefit from them.
2. Build Your Role Factory
-
IAM System Configuration
-
RBAC Program Methodology
-
More Roles (50+)
By the end of this phase you will have a team, policies and tools configured to create roles at speed without sacrificing access governance. Your IAM System will be fully configured to benefit from roles.

3. Run Your Role Factory
-
Roles (The rest of them)
In this phase the remainder of your role structure will be built until there are no longer valuable roles to create.