Top 5 Web Application Vulnerabilities
- August 28, 2023
- Posted by: admin
- Category: Blog
Web applications are like the doors to our virtual houses, protecting our sensitive information from cybercriminals. But just like a door might be left unlocked or have a broken lock, so too can online applications have weaknesses that attackers can take advantage of. In this blog, we’ll talk about the top five web application security flaws and how to fix them.
Broken Access Control: The system becomes vulnerable when access constraints are not effectively enforced, allowing unauthorized users to enter restricted regions or carry out unlawful actions. This can be avoided by putting in place suitable authentication and authorization measures, as well as testing and evaluating access restrictions frequently to make sure they’re working as they should.
Cryptographic failures: These flaws appear when cryptographic protocols like SSL/TLS are improperly set up or implemented. Attackers might be able to use this to intercept and decode sensitive data, including passwords and financial information. Utilizing robust, current cryptographic technologies and correctly configuring and maintaining them is crucial for reducing this risk.
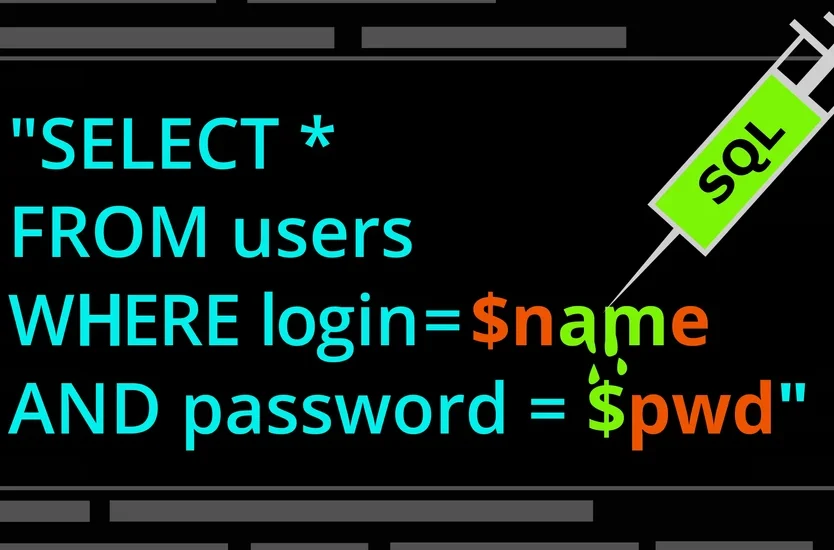
Injection: Typically characterized as OGNL injection, Expression Language Injection, command injection, and/or SQL injection, an attacker can inject harmful code into a web application, frequently through poorly validated input fields. As a result, the attacker may be able to access sensitive information or run arbitrary code on the server. When communicating with a database, it’s crucial to properly validate and sanitize all user input and to use prepared statements with parameterized queries.
Insecure Design: This vulnerability appears when a web application’s design is not secure, resulting in flaws such as a lack of input validation or lax password restrictions. Following best practices for web application development, such as using safe code frameworks and routinely testing and reviewing the program’s architecture, is crucial to reducing the risks associated with insecure design flaws.
Security Misconfigurations: This kind of weakness arises from the improper configuration of a web application, which might leave the server unsecure or expose unnecessary information in error messages. It is crucial to adhere to recommended practices for server and application configuration, such as using secure passwords and turning down unnecessary services, to reduce the risk of security misconfigurations.
Developers of web applications should be aware of these vulnerabilities and take precautions to avoid them. Using secure coding techniques, putting in place suitable authentication and session management rules, and frequently testing and updating programs are a few examples of how this can be accomplished. By doing this, we may contribute to the security of our web applications and guard against the compromise of important data.
To learn more about web application security, contact the experts at Identity And Access Solutions by visiting our website here